In the BAS Hacking series I am diving deep into the bowels of building automation networks and systems! I am going to take you through the full process of exploiting a system so that you can better understand the thought process of your attackers.
The series consists of 4 articles:
- BAS Hacking 101 Target Selection
- BAS Hacking 101 Scanning
- BAS Hacking 101 Exploiting
- BAS Hacking 101 Clean Up
BAS Hacking 101: Target Selection
In this, the first post of my BAS Hacking 101 series, we will discuss:
- Utilizing various websites
- Search engine commands
Tools Needed
In this article you will need the following:
- Web browser
- Internet Connection
Overview
Writing an article on BAS Hacking is seemingly more difficult than writing an article on generic web hacking. I have to walk a fine line between exposing holes in vendors and customers sites. I assume, the majority of people who will be reading this article will have access to their network and/or BAS systems and will be using this article to check for the public exposure and vulnerability of their systems. Because every system is different ever step in this series may not apply.
With that being said be sure to ask questions and provide feedback in the comments section. This will help us all become more educated. There are three, no actually there are four ways to find your target. The first and easiest way is if you already know the system type and network address of your targeted system. We won't explore this situation until part 2 of this series as that would make for a very short article. That brings us to the other methods:
Using the Web to Find Your Target
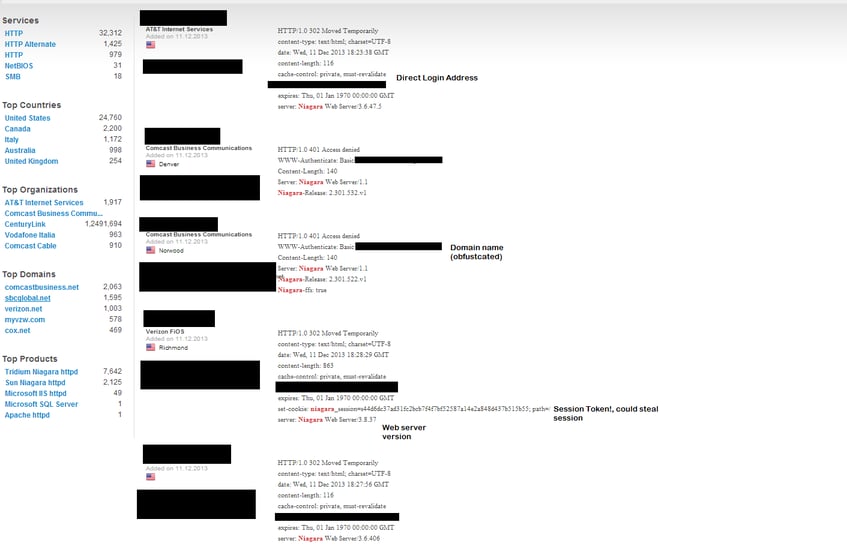
If you recall in my earlier articles I referred to ShodanHQ.com. Shodan is a spider of sorts that grabs banner data from well-known ports. It populates this data into a query engine from which you can find exposed systems. For example, if I was looking for a Tridium system I could simple type Niagara into my search and would be presented with a series of results.
As you can see the IP address, the version of the web server and other pertinent information is here. When we move on to port scanning having this IP address will be critical. Furthermore, having the version of Niagara that is running will be very important when we move onto vulnerability testing. Some of these IP addresses you will simply be able to connect to by typing in the IP address with the /login tab. In some cases the default username/password and/or no login exist which makes your exploration tasks quite simple.
Let's try looking for something more critical say a public service department... Scary stuff, I managed to find a School District and a State Agency. It's a good practice to try to search for your organization on Shodan. One more example to further demonstrate the danger of a site like Shodan. With Shodan, you can find older Niagara systems and their URL's. With this information you could connect to the server. You might get a screen that looks like this.
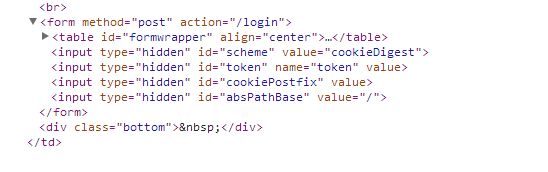
By trying the default user name and password you may gain access you or you may not. Fortunately with a web proxy you can eavesdrop on the session to give you access. I won't detail the exploit you can Google, Niagara base 64 as it is a public exploit and is in the public domain. Suffice to say by pressing F12 on my Chrome browser I can see that the web page had hidden fields that I also could exploit with a web proxy. 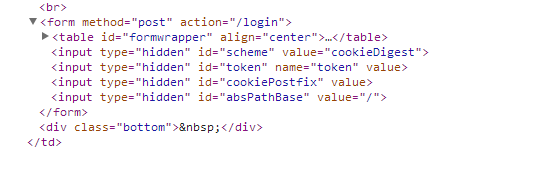
How to Prevent
The easiest way to prevent your system from being discovered is to not have it on a public network or a network that can be resolved through a public address. However, in most cases this is not feasible. So what is an owner to do? Obfuscation in this case is your friend. If you must have a web server for your BAS exposed you can take several steps to conceal its identity. First, you can ensure that your IP address doesn't resolve easily you can do this by:
- Hiding the WhoIs info, or using false info for your domain.
- Use an IP address that resolves to your ISP not your company's domain. For example Comcast in Dallas is not as helpful as Dallas/Fort Worth Airport.
- You can close ports 80 and 443 and force your web-server to use non-standard ports. This is not perfect as a full scan will find the open port but most non-professional crackers will scan well know ports to save time. You can also use an IDS like Snort to filter requests. Changing port 80 on your BAS is an undertaking in itself as most BAS's do not give you the option of using other ports.
- Keep your software up to date and patched.
Google the Most Powerful Target Tool Your Not Using
As I discussed you can use WhoIs to find out who the owner of an IP address is. You can additionally find out what IP addresses are under a domain. When you have a list of IP addresses you can perform multiple methods to find which machine has a BAS system on this. You can utilize scripts to run through the list of IP addresses appending a /login tag at the end of the IP address. However, if the organization is running any form or Intrusion Detection System (IDS) your recon will light up like a Christmas tree. So it is here that we turn to Google to help us with some passive reconnaissance.
When Johnny Long, published his findings on the ability to use Google as a hacking tool the hacking community was definitely abuzz. Even though this method was released several years ago we find that using Google and its associated search primitives can help you narrow down on key information.
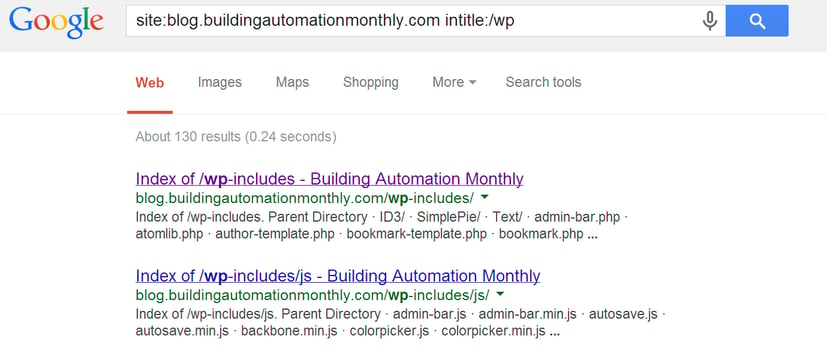
I had to think to myself on how to best demonstrate this because ethically you should only be performing these queries against a site if you have permission. So what I did was I went and ran some of the queries against my own blog so you could see the results.
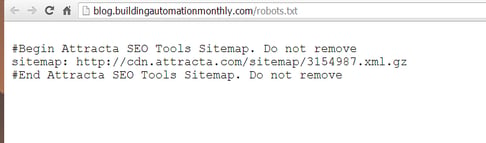
As you can see, by using search primitives I was able to focus on my site and see all of the directories that lie within this site. Typically a web administrator would have a robots.txt file configured to hide these paths from a search engine but that would kill our example.
As you can see I used the site: and the inurl: primitives to narrow down my search. An extensive list of primitives and current queries is here.
Later on I can use this information to exploit this web server. I could use this information to take control of the machine that is running the BAS. For example, if I knew the IP address of the machine on which my BAS system resided but I could not access the BAS I could penetrate the machine, gain root access, grab the BAS password files (many of which are in plain-text or a simple MD5 hash) and then could reverse engineer login credentials.
Listed below are the more common Google primitives and their function.
- Site: this defines the site within which Google should search, often this is used with the intitle or inurl primitives for example site:abc.com inurl:/admin
- intitle or allintitle: These define words that would be in the HTML title of the web resource. For example allintitle:admin would pull websites that have admin in their title. Do not confuse this with inurl.
- allinurl or inurl: This tells Google to search for certain words within the url for example index or admin.php which will find the php code for admins at specific websites.
- filetype: This can often be used with the Site primitive in order to search sites for files. Often times documents like password files or username files will be left on a site.
In addition to these sources there is also the "WayBackMachine". This allows you to search cached versions of older websites that may have been updated or deleted. This is a great way to find potential links that have been removed that will allow you access to the web server. Using this along with the Robots.txt file you can find directories that may expose vulnerabilities.
What IP Range do I search?
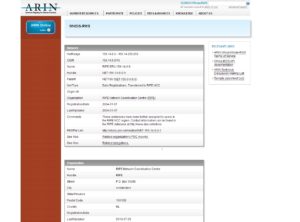
ARIN, the American Registry for Internet Numbers. Provides a tool called Who-Is. This allows you to search for the IP range of your target. Using the ShodanHQ example. When I find a public IP address from a Niagara BAS Engine I can take that address and enter it into the ARIN who is search at WHO-IS. This will provide the point of contact, length of registration, IP address range and various other important information. Here is a sample Who-Is request to a random IP address.
Final Notes
Before I close this article I will address a question I am asked quite often. I have had several people as me why should they care about reconnaissance? What does penetrating a web server or physical server have to do with a BAS system? Oftentime's BAS systems are installed on older Operating Systems and are done outside of an organizations IT department. This means that a device may exist on a organizations network that is un-patched and un-monitored.
Often times when people seek to penetrate a BAS system it is not because they want to control the BAS system. They choose the BAS system as a target because of the following reasons:
- BAS's are unfamiliar to IT folks so they don't know if the connection to a port is normal or not. Because of this it is often ignored.
- BAS's are installed or were installed without the IT departments knowledge and act as a perfect foothold to penetrate a network.
- BAS's are often unpatched because patching the web server could disrupt the BAS software. This means that exploits exist that would normally be patched in a production environment.
Conclusion
This was a good start for the series and I got a lot of feedback around the desire to see more. This is possibly the most important step in testing any system. If you do not conduct proper research you will often find the wrong target if you find any target at all. Thus it is critical to conduct your research. Additionally, if your exploiting fails and you need to switch to a social engineering approach it will be critical that you know the information in this article.
In the next article, we will discuss active enumeration, using tools like NMAP and Wireshark to perform analysis of the BAS network.
What are you doing to ensure your systems are secure?
Do you need some ideas? Share your thoughts in the comments below!